Phishing attacks have become an all too common threat in modern society, impacting individuals and businesses alike.
With an average of 31,000 phishing attacks occurring daily, it’s clear that scammers are constantly devising new ways to exploit unsuspecting victims. These attacks can lead to devastating financial losses and emotional stress.
In this article, we’ll explore what phishing is, the various types of phishing attacks, and what can be done to prevent them. If you’ve been a victim of phishing, we’ll also discuss how CEL Solicitors can help you recover.
Phishing: A Definition
Phishing is a form of cybercrime where scammers attempt to deceive individuals into sharing sensitive information, such as passwords, credit card details, or personal identification numbers. These attacks typically occur through emails, text messages, or malicious websites that mimic legitimate sources. By creating a false sense of trust, phishers trick victims into revealing confidential information or performing harmful actions, like clicking on malicious links.
How Does Phishing Work?
Phishing attacks generally follow a predictable pattern:
The Hook: The attacker sends a convincing message designed to look like it’s from a trusted source, such as a bank, employer, or online retailer.
The Bait: The message creates urgency or fear, prompting the recipient to act quickly without thinking critically. Examples include warnings about account suspensions or offers too good to be true.
The Trap: The victim clicks a link or downloads an attachment, which either directs them to a fake website or installs malicious software on their device.
The Catch: The attacker collects sensitive information entered by the victim or gains unauthorised access to their accounts.
Types of Phishing Attacks
Phishing comes in various forms, each targeting victims differently. Below, we’ll delve into some of the most common types of phishing attacks.
What is Spear Phishing?
Spear phishing is a highly targeted form of phishing. Unlike generic phishing attacks, which are sent to large numbers of people, spear phishing is tailored to a specific individual or organisation. The attacker often researches how to make their message appear credible, using personal details to establish trust. For instance, an email might reference a recent business transaction or include the recipient’s name and job title.
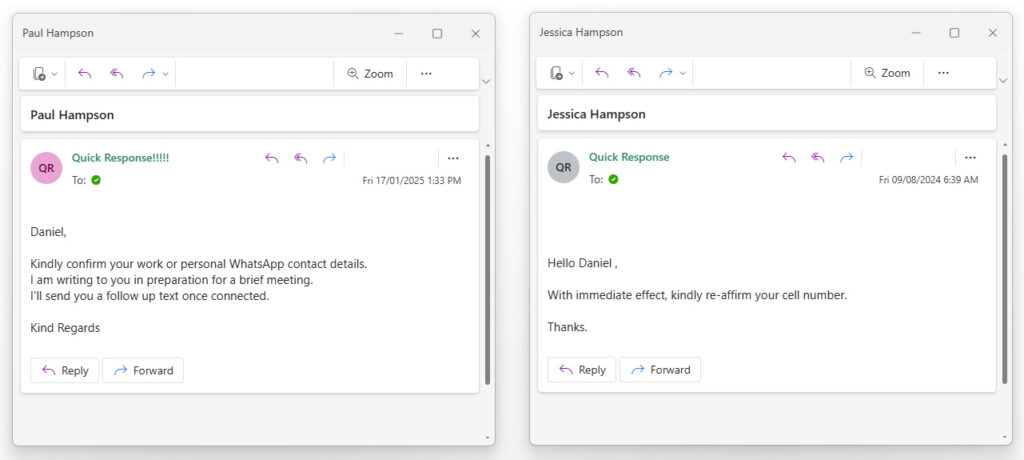
Example of a spear phishing attack: Scammers impersonate CEL Solicitors’ owners, Jessica and Paul Hampson, to target staff members.
Above are two very real examples of spear phishing attempts by scammers.
At first glance, it may appear legitimate, and for those who work in large organisations or who may not recognise when their colleague or employer is using wording that they wouldn’t usually, this can be a very effective way of deceiving people.
What is Clone Phishing?
Clone phishing involves creating a near-identical copy of a legitimate email or message previously sent by a trusted entity. The scammer modifies the original message to include malicious links or attachments and then sends it to the victim, often from a spoofed email address that appears genuine. Because the message mirrors something the recipient has seen before, it’s easier to fall for this type of attack.
What is Whaling?
Whaling is a type of phishing attack that specifically targets high-profile individuals within an organisation, such as executives or senior managers. These attacks often involve elaborate schemes to extract sensitive company information or authorise large financial transactions. Whaling messages typically appear highly professional and may have insider knowledge to make the scam more convincing.
Emerging Phishing Concerns
The evolving tactics of cybercriminals have led to growing concerns among cybersecurity experts. For instance, 61% of cybersecurity leaders are worried about the use of chatbots in phishing, as these AI tools can craft convincing messages on a large scale. Furthermore, 63% of cybersecurity leaders are concerned about the creation of deepfakes for phishing purposes, highlighting the increasing sophistication of these attacks.
Key Differences Between Types of Phishing
While all phishing attacks share the goal of deceiving victims, the key differences lie in their approach and targets. Spear phishing is personalised to individuals, clone phishing mimics legitimate communications, and whaling focuses on high-value targets within organisations.
How to Prevent Phishing Attacks
Preventing phishing attacks requires people to be aware and take proactive measures. Here are some tips to protect yourself:
Strong Passwords: Use strong, unique passwords for each of your accounts, and enable two-factor authentication (2FA) whenever possible.
Verify Sources: Before clicking links or sharing information, verify the sender’s identity. Be cautious of unsolicited messages.
Watch for Red Flags: Look out for spelling errors, generic greetings, and a sense of urgency—all common signs of phishing messages.
Update Software: Keep your devices and security software up to date to protect against vulnerabilities.
Educate Yourself: Learn about common phishing tactics and share this knowledge with others.
Have You Been Scammed? CEL Solicitors Can Help
If you’ve fallen victim to a phishing attack, you must act quickly. At CEL Solicitors,we specialise in helping victims of scams, including phishing attacks. Our experienced team can guide you through the recovery process, working on a no-win, no-fee basis to ensure you get the support you need without financial risk.
We’ve successfully helped many clients reclaim their money and regain peace of mind. If you’ve been scammed, contact us today for a free consultation and take the first step toward justice.